Modern businesses thrive on seamless and efficient communication, with the business phone system serving as its backbone. While traditional phones were once reliable, they now pose limitations. Once stalwarts of business communication, they are now proving to be expensive relics.
In a recent study, a majority of IT and non-IT leaders say technical debt severely limits their IT function’s ability to innovate and migrate to new technologies. On top of that, many businesses report allocating significant funds and budget towards sustaining business operations. This means, less is available for innovation as time and money is spent maintaining, fixing, and damage control.
As technology advances, maintaining outdated phones can incur unforeseen costs, hindering business efficacy. In this article, we cover the factors that affect legacy phone system cost and how you reduce your communication expenditure with alternatives like voice over internet protocol (VoIP).
How Much Do Legacy Phone Systems Cost? Key Factors
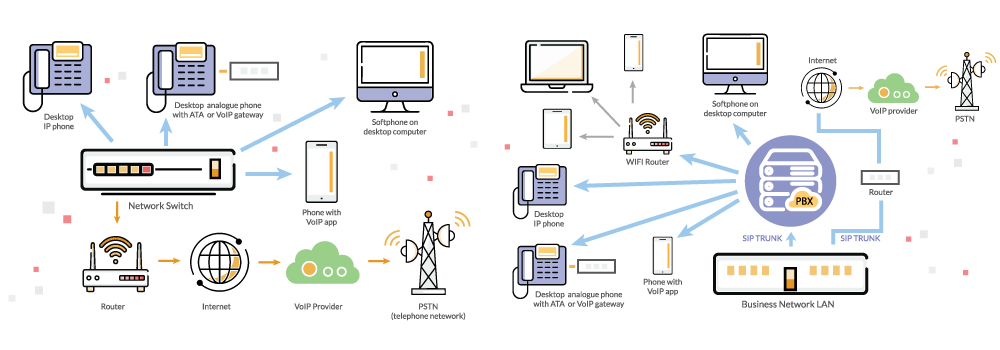
Legacy phone systems refer to traditional business phone systems that have been used for decades. These systems transmit analog or voice signals through copper wires between users. The most common examples of legacy systems are the Public Switched Telephone Network (PSTN) and the Plain Old Telephone Service (POTS). Legacy systems are characterized by their reliance on physical hardware, such as landline phones and on-premise PBX systems.
Knowing how much your legacy phone system is costing you is essential to understanding your communication expenses. From unexpected outages and downtime to call volume charges and hardware upkeep, each aspect contributes tremendously to the big picture. Let’s look at the key factors contributing to the true cost of a legacy phone system.
1. Outages and Downtime
Hardware failures, network issues, low-quality IT infrastructure, and bad weather are some factors that can trigger outages, disrupting the ability to make and receive calls. This interruption could affect communication with customers, suppliers, and stakeholders. Such downtime can ultimately impact revenue generation and tarnish brand reputation.
Still, businesses are reluctant to move to newer, more efficient technologies. In contrast, VoIP and internet-based phone systems offer redundant and high-availability networks that ensure continuity and keep the business running as usual.
2. Call Volume and Usage Charges
One key factor contributing to the higher costs of legacy systems is the method of call routing and transmission. Calls made through legacy systems typically travel over the PSTN. When you make a call, a dedicated circuit is created between the point where your call originates and the point serving the person you’re calling. This circuit allows your voice signals to travel through the network from your phone to the recipient’s phone.
However, the establishment of these circuits comes with costs, particularly when the call crosses long distances. For long-distance calls, more infrastructure and resources are required to establish and maintain these circuits, resulting in higher costs for both the telecom provider and the user. Plus, getting more phone lines means adding new infrastructure, which costs a lot of money.
3. Hardware Upkeep and Support
Legacy phone systems rely on outdated hardware components like analog lines, physical switches, and handsets that may need to be replaced periodically due to wear and tear, which can contribute to ongoing costs.
Additionally, they need IT staff with the right expertise and skills to maintain operations daily. However, as newer phone systems continue to grow popular and become the norm, fewer people know or are willing to deal with older systems. Hiring the right people to work with such technology can, therefore, prove expensive.
Adding to that, failure to maintain these systems could result in service disruptions, which further entail financial repercussions for the business.
4. Limited Flexibility and Scalability
A legacy phone system offers limited flexibility and scalability, and you might need to allocate more of your infrastructure budget. For instance, adding new phone lines or expanding infrastructure—like purchasing additional hardware and phone lines—means additional spend. Naturally, this will lead to increased complexity and cost.
While traditional phone systems allow call merging and routing, you may require staff to handle these tasks manually. If this manual intervention is insufficient or unmonitored, especially in high call volume settings, you may experience missed opportunities and revenue loss.
Further, the absence of advanced call management features (like transcription, IVR, and auto-attendant) and modern solutions (like integrations with other business systems) make legacy phones incompatible with remote and hybrid work setups. Modern businesses demand mobile, flexible, and easily scalable communication solutions, and lack thereof adds to the overall cost. However, adding these features to your legacy phone system will stack up as more hidden costs.
VoIP, on the other hand, typically comes packed with advanced features and call management functionality. Read more about VoIP features ahead.
5. Staff Training
Training and skill development are essential for all those who manage legacy phones. While using a legacy phone might seem straightforward, there are still essential functions that employees need to understand, such as call forwarding, conference calling, and using voicemail. Proper training ensures that employees know how to use the phone system efficiently, reducing the likelihood of missed calls and minimizing downtime.
However, training staff over time can be an ongoing expense. This includes costs for initial training as well as recurrent training for updates or new features.
Cost Advantages of VoIP Business Phones
Many organizations are transitioning to modern and flexible communication solutions, such as VoIP and session initiation protocol (SIP), to mitigate costs associated with legacy systems. This migration presents an opportunity to streamline communication processes and reduce costs. Basically, VoIP/SIP lets you upgrade telephony service but decreases costs.
VoIP leverages software-based platforms and internet infrastructure to offer a spectrum of cost benefits compared to legacy phone systems.
Let’s explore the key factors that contribute to its affordability and effectiveness in modern business operations:
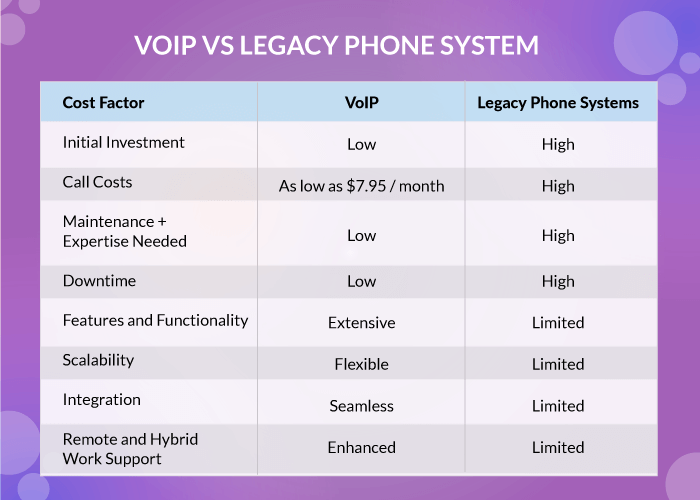
1. Initial Investment
VoIP relies on software-based solutions and utilizes existing internet infrastructure, reducing upfront costs. This means you can use it to add new functionality to your existing structure. Or, do away with your outdated equipment and forward calls to your computer or laptop using a VoIP softphone.
In fact, United World Telecom offers a flexible softphone and web dialer with our outbound calling plans, so your teams can connect from anywhere.
2. Call Costs
VoIP providers often present more competitive pricing structures, particularly for long-distance and international calls. For instance, United World Telecom offers plans for as low as $7.95 per month and they come with a host of free call management features.
Additionally, we offer extensive voice global coverage, reaching even the remotest locations at cost-effective rates. Our connectivity spans over 160 countries, allowing you to engage with customers worldwide. Furthermore, by forwarding calls virtually, you don’t need to worry about additional long-distance rates.
Get a toll-free number and facilitate cost-free communication for your global customer base. And if you choose local numbers, customers still call at low local rates, even if you forward those calls internationally.
3. Maintenance Costs
VoIP is a cloud service, which means it is hosted and maintained by service providers. This way, you don’t have to worry about maintenance and upkeep at all. From routine updates to troubleshooting and repairs, the responsibility falls squarely on the VoIP provider’s shoulders, freeing up valuable time and resources for you to focus on core business operations.
4. Downtime Costs
VoIP systems are inherently more resilient to downtime with the availability of features like redundancy routing and failover forwarding. These features are proactive measures that automatically redirect incoming calls to alternative destinations in the event of system failure or network disruption. All you have to do is set up routing rules to specify alternative phone numbers, extensions, or voicemail boxes where calls should forward to during downtime.
To improve phone system reliability, check out our resource on VoIP uptime.
5. Features and Functionality
Service providers like United World Telecom offer an exhaustive list of cloud telephony features and functionalities unavailable with traditional legacy systems. From time of day and VIP caller routing to advanced IVR and call flow builder, the list of options is endless! You can use these VoIP features to reduce costs as they come free and can be implemented in an online control panel. So, no extra hard or software investment is required.
Additionally, these features can help cut down on time-consuming tasks, improving operational efficiency. For instance, while legacy phone systems can send voice calls to voicemails, an agent or staff must manually listen to the messages and jot down important details. Additionally, if you have a global customer base, you’ll need a translator to interpret or translate transcripts. But with a business voicemail translation feature, you can get the voicemails transcribed and translated in your preferred language on a single platform. This way, global teams can efficiently communicate and collaborate regardless of where team members are located.
6. Flexibility and Scalability
With VoIP, you get unparalleled flexibility and scalability to adjust your communication infrastructure according to changing business needs. You can add or remove users, phone lines, and numbers in a simple few steps—all this without investing in costly hardware upgrades.
7. Integrations
One of the best aspects of VoIP telephony is it seamlessly integrates with other business applications and tools, allowing for greater efficiency and workflow automation. Integrations with CRM software, email platforms, and collaboration tools streamline communication processes and eliminate the need for manual data entry, resulting in time and cost savings.
United World Telecom offers the option to connect your phone numbers to your business tools like Zoho, Salesforce, Zendesk, and more. Visit our integrations page or speak to one of our experts to learn all about this telephony capability.
8. Remote and Hybrid Work Support
VoIP systems are well-suited for remote and global environments, providing employees with access to the same communication features and functionalities regardless of their location. With mobile apps, softphones, and web-based interfaces, remote workers can stay connected and productive without the need for additional hardware or infrastructure, reducing overhead communication costs.
As you can see, the total cost of ownership for VoIP systems is generally lower than that of legacy phone systems due to lower infrastructure costs, reduced call rates, and increased efficiency and productivity gains.
You can read more about why VoIP is a good fit for distributed teams in our article.
How Can UWT Help?
Legacy phone systems are undoubtedly becoming obsolete. Latest technologies like SIP and VoIP come with endless possibilities in communication that can grow your business.
Is VoIP a reliable alternative?
Yes, VoIP is highly reliable and has globally emerged as a preferred alternative to legacy phones. We at United World Telecom have helped global businesses evolve with our VoIP offerings since 1996.
UWT offers basic to advanced VoIP-based call management features catering to different business communication needs. We also understand the complexities of upgrading from legacy phones to VoIP.
Don’t let outdated technology hold your business back!
How to switch to VoIP?
Switching to VoIP involves planning, testing internet connectivity, preparing infrastructure, selecting a provider, choosing equipment, training teams, and setting up your device for a smooth migration.
Stay ahead of the curve in the digital age. Consult with our experts today and let us help you transition to VoIP.
 Network & Reliablity
Network & Reliablity Country Coverage
Country Coverage Testimonials
Testimonials Customer Stories
Customer Stories Local 2-Way Voice
Local 2-Way Voice Toll Free Numbers
Toll Free Numbers Local Phone Numbers
Local Phone Numbers Toll Free FlexDial
Toll Free FlexDial BYOC
BYOC Outbound Calling
Outbound Calling SIP Trunking
SIP Trunking Call Forwarding
Call Forwarding AI Call Insights
AI Call Insights Call Transcription
Call Transcription IVR Auto-Attendant
IVR Auto-Attendant Analytics & Reporting
Analytics & Reporting Call Recording
Call Recording Time-of-Day Routing
Time-of-Day Routing Voicemail
Voicemail Salesforce
Salesforce HubSpot
HubSpot Zoho
Zoho  MS Teams
MS Teams  Genesys PureCloud
Genesys PureCloud 3CX
3CX Zendesk
Zendesk  Intercom
Intercom Gorgias
Gorgias Onboarding
Onboarding Knowledge Base
Knowledge Base Blog
Blog