Legacy phone technologies, like the PSTN and on-premise PBX systems, shaped digital communications today, but it’s time for businesses to embrace the digital landscape’s growing needs.
This is especially important for virtual and hybrid work setups. Employees, stakeholders, partners, and customers can connect from anywhere, using features like virtual extensions and global SIP trunking.
But with more and more businesses using cloud-based communication, securing your cloud PBX phone system is crucial.
In this guide to PBX security, we’ll go over:
- Which is more secure? Cloud PBX or On-Premise PBX
- Potential threats
- Best practices of PBX security
Importance of Keeping Your PBX Phone System Secure
It’s necessary to use cybersecurity measures to protect communication data handled by your cloud PBX from potential threats and unauthorized access. These cyberattacks can result in high costs (up to $10.5 trillion annually by 2025), data loss, and cause lasting damage to your business reputation. In the U.S., in 2022 alone, there were countless malware attacks (44%), data breaches (27%), and DDoS attacks (22%) (Forbes).
And yet, most companies don’t invest in cybersecurity because they have “little financial incentive to do so.” However, when organizations have advanced security measures and capabilities, they can deliver 43% higher revenue growth. This means that if your business is not paying attention to security across the board, you are not safeguarding your business enough.
This is true even in the case of a cloud telephony or PBX system, primarily because they rely on the internet to function.
Is Cloud PBX or On-Premise PBX More Secure?
Whether cloud PBX or on-premise is more secure depends on a few factors such as communication needs, budget, provider, and IT team availability.
The main difference between cloud and on-premise PBX systems is where they are stored and who is in charge of the system. Cloud PBX is typically hosted by your PBX provider and available through the Internet. Since it’s a hosted system, your provider maintains, updates, and secures the system. While cloud communication technology is convenient, cost-effective, and easily accessible, if not secured well, it can be prone to fraud, breaches, and similar disruptions.
On-premise PBX, on the other hand, is located in your office premises and connected to your internal network. This is typically built, run, and managed by your experienced in-house IT team. Since your team is in charge, you have more control over how to keep your system secure. Yet, on-premise systems can be outdated compared to modern technology, and by extension, modern cybercrimes. This may lead to struggles with functionality, recovery, and stability.
Learn more in our guide on cloud vs on-premise PBX.
5 Potential Threats to PBX Security
Identifying and fixing security issues begins with understanding the different cybersecurity problems and what elements they can affect. From the menace of eavesdropping to sophisticated cyberattacks, several threats make your cloud PBX system vulnerable. Here are a few of them:
1. Unauthorized Access and Hacking
2. Denial of Service (DoS) and Distributed DoS (DDoS) Attacks
3. Eavesdropping Attacks
4. Malware Attacks
5. Phishing and Social Engineering
5 Best Practices of PBX Security
Securing your cloud PBX system is paramount, and implementing best practices ensures its resilience against potential threats and attacks. From fortifying your system with robust passwords to bolstering its defense with modern technical measures, here are some ways to protect your PBX system:
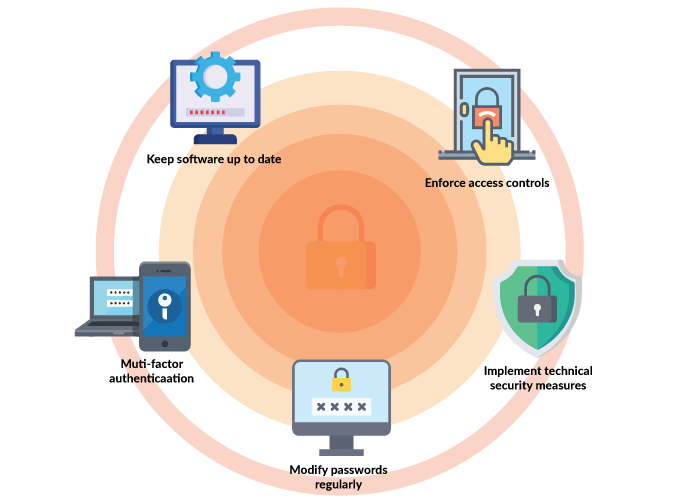
1. Password Fortification
Use long, complex, and strong passwords for your PBX phone system and update them regularly. Change default admin and guest passwords to something uncommon to avoid common attacks. These simple steps replace easy-to-guess passwords, reducing the risk of common attacks.
2. Multi-Factor Authentication (MFA)
Now, most PBX and VoIP providers offer two-factor authentication (TFA) or MFA as part of their service. Users must provide a verification, like a code sent to their email, along with their password to get into the account. This way, even if an attacker gets a user’s password, they can’t get in without the verification code. Enable these defenses for all user accounts for an added layer of security. Also, remember to check and update MFA settings periodically.
3. Software Updates
Make sure both your PBX provider and your business update the software regularly. Providers should fix bugs and security concerns and release timely software upgrades. And users must make sure to apply all the latest security patches and updates. This helps fix security issues and address potential vulnerabilities.
4. Control Access
Set up controls to decide who can access what. It ensures that only the right people can use and manage the communication system, keeping sensitive information safe. By assigning specific permissions and restrictions, you can mitigate the risk of unauthorized usage and cyberattacks. This proactive measure enhances the overall system resilience.
Learn more about our user and role management features.
5. Technical Measures
Intrusion detection systems and firewalls help in monitoring and blocking suspicious activity. Employ encryption to shield communication data, especially in VoIP calls, videos, text messaging, and other communication-related data. Encryption converts data into secret texts accessible only through a decryption key that converts it back to its original form. This protects the data from unauthorized access.
In addition to that, use digital certification, VPNs, and other authentication protocols to verify device and user identities, preventing breaches. Proactively audit network, system, and access logs and user accounts for unusual usage patterns.
These technical measures, combined with established practices, offer robust protection against unauthorized access and threats to your PBX security.
Learn more in our guide to VoIP security.
6. Educate and Train Users
Nothing helps keep systems secure like teaching your users the dos and don’ts of IT security best practices. Do refresher training, set up reminders to change passwords, conduct regular service checks, and so on.
How Can UWT Help?
As more businesses use cloud-based communication, it’s crucial to prioritize strong cybersecurity and safety measures. Since 1996, United World Telecom has provided secure and reliable VoIP services. We know that security is important for high-quality, fraud-free VoIP calls. Get in touch with us now for any questions about improving your business communication system and protecting it from security risks.
Call us at 1 (877) 898 8646 and learn more about our privacy, security, and fraud control measures.

